
Keeping Your Business Secure Starts with Educating Employees About Cyber Security
By: Danielle HovermanNovember 21, 2017
Training employees on cyber threats is the key to a successful cyber security protection program. 6 tips for educating employees about cyber security.

How to Spot Common Cyber Scams
By: Danielle HovermanNovember 21, 2017
It’s important to understand common cyber scams and how to avoid them including: inbox scams, malicious websites and malvertising, and pop up scams.

5 Types of Social Engineering Scams
By: Danielle HovermanNovember 21, 2017
The five most common social engineering scams that attackers use to target their victims include: phishing, baiting, quid pro quo, pretexting, and tailgating.
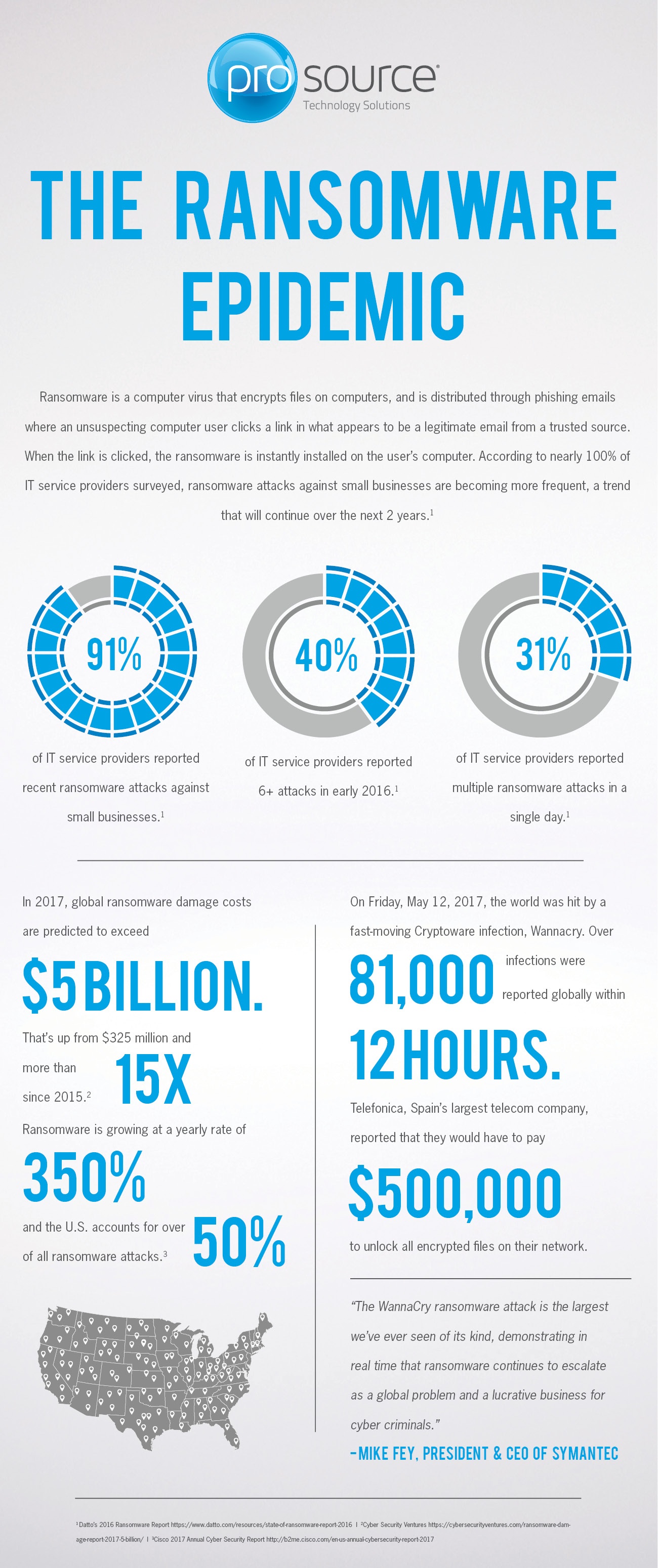
[Infographic] The Ransomware Epidemic
By: Danielle HovermanNovember 21, 2017
Ransomware is a computer virus that encrypts files on computers. View this infographic to learn about the ransomware epidemic

5 Benefits of Attending Prosource Tech Show IX
By: Danielle HovermanSeptember 11, 2017
Here are 5 reasons why you should attend Prosource Tech Show IX, presented by Konica Minolta on Wednesday, October 25, 2017 from 10am-2pm at Paul Brown Stadium.

Giant Equifax data breach: 143 million people could be affected
By: Sara Ashley O'BrienSeptember 8, 2017
Equifax says a giant cybersecurity breach compromised the personal information of as many as 143 million Americans — almost half the country.

Company moving its Dayton branch to Austin Business Park
By: Cecilia SalomoneAugust 30, 2017
Prosource has announced plans to move its Dayton branch office to Austin Business Park this fall as part of the office technology company's expansion.

Can You Answer These 8 Questions About Cyber Security in Your Business?
By: Danielle HovermanJune 19, 2017
Can you answer these 8 questions about cyber security in your busienss?

A Closer Look at Ransomware
By: Danielle HovermanJune 13, 2017
Ransomware has the capability to completely disable businesses of any size and type. Here is what you need to know about ransomware.
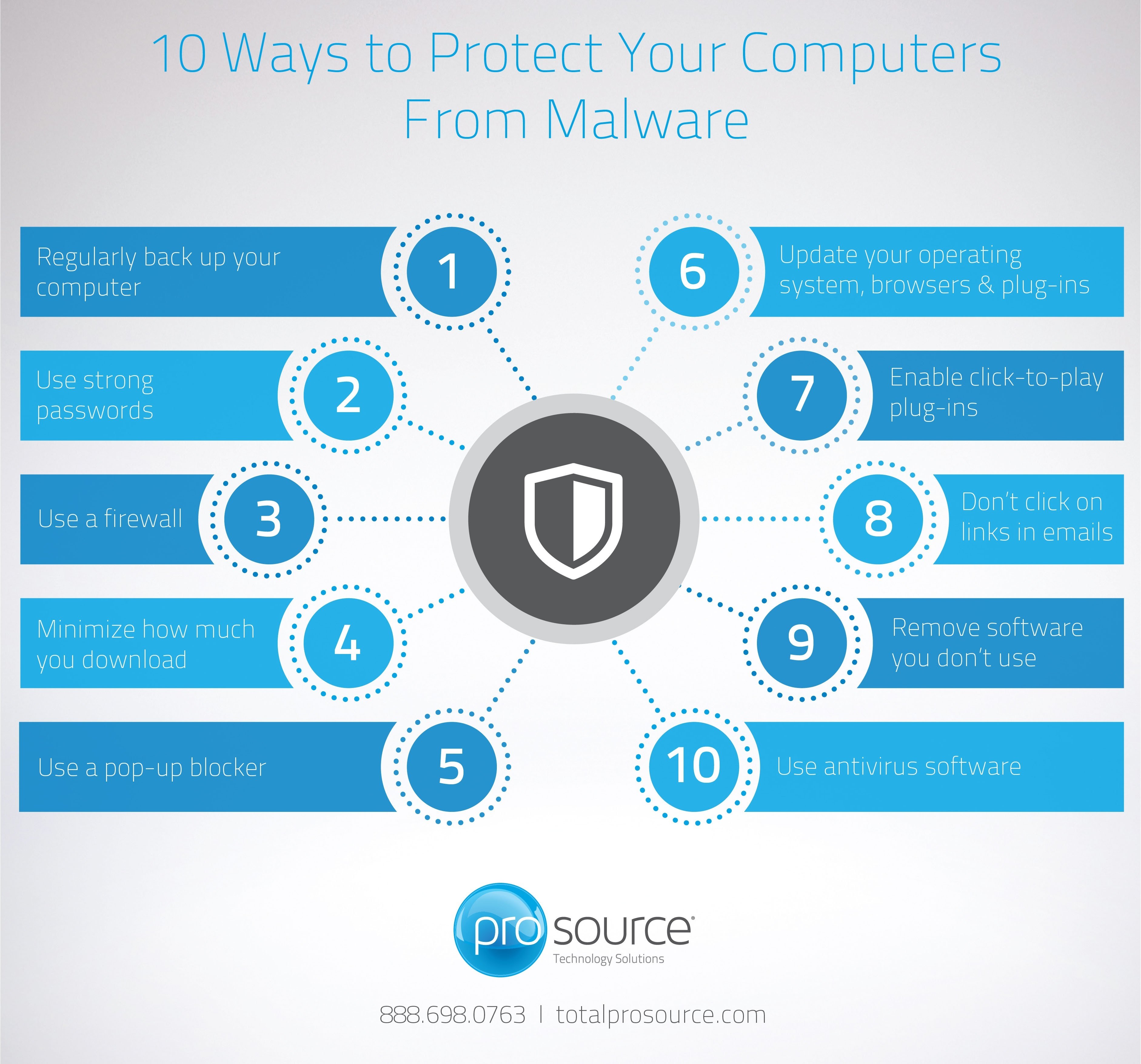
10 Ways to Protect Your Computers From Malware
By: Danielle HovermanJune 13, 2017
Here are 10 ways to protect your computers from malware.
