 Click on the image to enlarge
Click on the image to enlarge
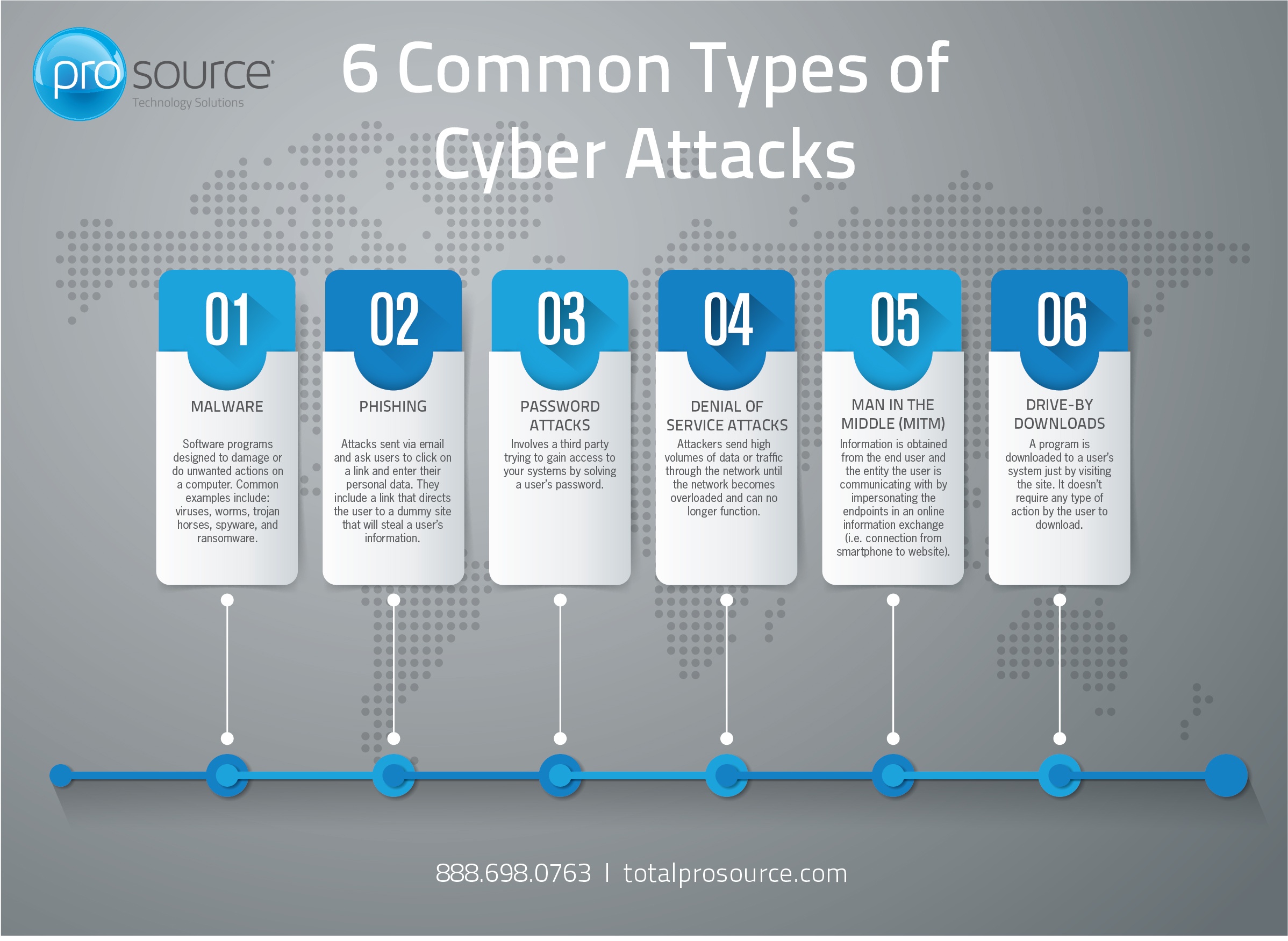
A cyber attack is any type of offensive action that targets computer information systems, infrastructures, computer networks or personal computer devices, using various methods to steal, alter or destroy data or information systems. This infographic outlines 6 common types of cyber attacks you should know about
1. Malware
Software programs designed to damage or do unwanted actions on a computer. Common examples include: viruses, worms, trojan horses, spyware, and ransomware.
[You Might Also Like: Blog Article - "How to Prevent Common Cyber Attacks"]
2. Phishing
Attacks sent via email and ask users to click on a link and enter their personal data. They include a link that directs the user to a dummy site that will steal a user’s information.
3. Password Attacks
Involves a third party trying to gain access to your systems by solving a user’s password.
[You Might Also Like: Blog Article - "5 Common Types of Malware"]
4. Denial of Service Attacks
Attackers send high volumes of data or traffic through the network until the network becomes overloaded and can no longer function
[You Might Also Like: Blog Article - "10 Ways to Protect Your Computers From Malware"]
5. Man in the Middle (MITM)
Information is obtained from the end user and the entity the user is communicating with by impersonating the endpoints in an online information exchange (i.e. connection from smartphone to website).
[You Might Also Like: Blog Article - "Layered Security Key to SMB Cyber Protection"]
6. Drive-by Downloads
A program is downloaded to a user’s system just by visiting the site. It doesn’t require any type of action by the user to download.