Three Common Email Scams that Can Sneak Past Your Spam Filter
When we think of email security, we usually think of messages with dangerous links and attachments meant to infect our devices with a virus.
But not all malicious emails contain malware; many contain clever cons designed to trick you into sending money or providing access to your password-protected accounts.
These email attacks usually involve phishing. “Phishing” refers to a kind of cybercrime where scammers try to fool you into performing an action, such as sending them money or revealing personal information online. The name comes from the idea of fishing: scammers send a message that acts as bait, hoping to “hook” you.
In the war against cybercrime, we have tools that filter email and internet traffic to protect us from known viruses, but it’s difficult for a software program to detect and protect us from cyber criminals attacking us with words instead of viruses.
Real-Life Examples of Email Scams
To protect yourself, you need to know the common types of attacks that can get through your spam filter and be ready to play defense. Here are three examples we’ve seen in real life:
- An accounting employee received an email from the president of her company. In the email, he asked her to make an electronic payment to the account listed or else the vendor wasn’t going to sell them the materials needed to complete a major project. She made the payment of nearly $10,000. The email was a scam.
- Several employees in one company received an email directing them to verify their email address and password to prevent their accounts from being locked out. Only three people fell for the scam, but three was enough. The company’s email was compromised and used to send malware to everyone in their contact list.
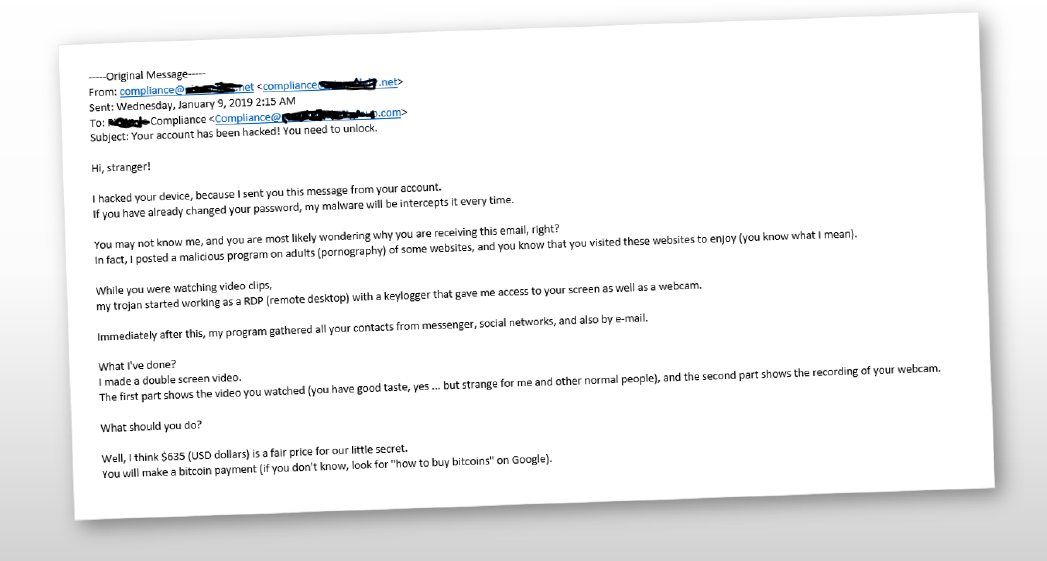
- A lawyer received an email from what appeared to be his own email address. The scammer stated that he had total access to the lawyer’s computer and threatened to send the lawyer’s browser history to everyone in his contact list unless the lawyer sent $500 in bitcoins. The email even listed the lawyer’s password. Worried and embarrassed, the lawyer sent the money.
In the three stories above, the malicious emails made it past email filters because they don’t include any virus files or links to blocked sites for the filters to detect.
Business Email Scams
The first was an example of a business email scam, in which a scammer determines who handles accounts payable for a company by searching on the company’s website or social media profiles. The scammer sends that person an email to trick them into paying money.
Business email scams take different forms. Sometimes, they try to get the victim to update a bank account number on file for an employee or vendor. The result is that all payments to that account are stolen, and the employee or vendor still expects to get paid. Other times, these scams mimic the email of a high-ranking employee and make an urgent plea for funds to be transferred or for gift cards to be purchased. Scammers will even figure out if the CEO is traveling and make requests for emergency funds, citing a lost credit card or stolen luggage.
Credential Phishing
The second story is an example of credential phishing. In this scam, the scammer creates a website that looks identical to a cloud service provider. The scammer then sends an email prompting the target to click the link, which leads to a login page that looks like the login page for the cloud service provider. When the user enters their username and password, they are giving their login credentials to the scammer.
Extortion Scams
The third story is a common extortion scam, where the scammer pretends to have embarrassing information about the target. The scammer sends an email and “spoofs” it to look as if it is coming from the target’s own email account. The email threatens to send the target’s browser history and images pulled from the webcam to everyone in the target’s contact list.
While this scam feels personal, it is actually a numbers game. Scammers pull email and password combinations from databases on the dark web and send out email after email, searching for the 3% of people with both a guilty conscious and disposable income.
With the average business user receiving and sending more than 120 emails a day, it’s no wonder that even the savviest user occasionally takes the bait and clicks on the wrong thing.
That’s why it’s so important that we all take responsibility when it comes to email security—and overall cyber security. Awareness and education are key. Do you know how to spot an email scam and protect yourself when one inevitably lands in your inbox?
Learn more in our next Cyber Security Awareness Month blog, "Email Scams: 13 Ways to Protect Yourself and Your Organization."
At Prosource, we believe your organization’s security is only as strong as its weakest link, so for National Cyber Security Awareness Month, we're taking a more personal approach to awareness. You can also check out our LinkedIn, Facebook, and Twitter pages for cyber security tips and tricks.

