For many years, businesses have protected their valuable and sensitive information by building a fence around those assets using endpoint protection and firewalls. All the data that flowed in and out of the business was either via a single internet access point or on physical devices. Despite increased coverage of security breaches, many businesses are still trying to protect their networks using traditional firewalls and other outdated security solutions.
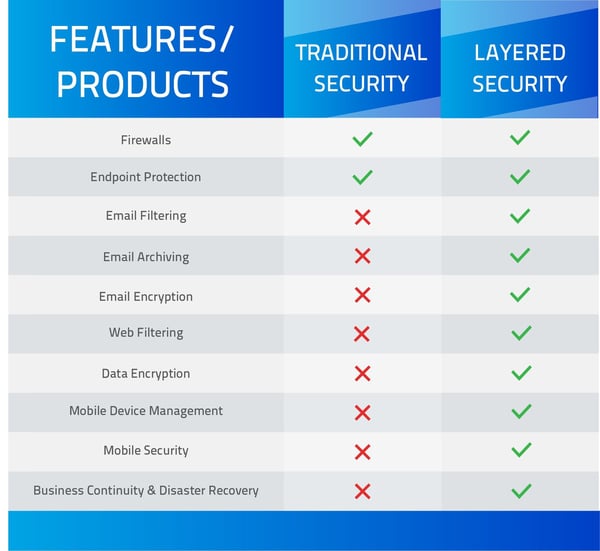 Above is an example of what features/products your business would have under a traditional vs. layered security plan. Click the image to enlarge.
Above is an example of what features/products your business would have under a traditional vs. layered security plan. Click the image to enlarge.
SMBs continue to be at increased risk for security breaches. In 2017, the damage or theft of IT assets and the disruption to normal operations caused by cyber attacks cost SMBs an average of $2,235,000.[1] It’s clear that traditional approaches to security are no longer effective in the reality of today’s complex cyber threat landscape. By not looking at cyber security from a holistic viewpoint, through training and awareness as well as looking at facilities and processes, many businesses have gaping holes in their security efforts.
[You Might Also Like: Blog Article – “What is Layered Security and How Does it Defend Your Network?”]

Security risks can occur at any level in your IT infrastructure. This means that you need to set up security measures that provide multiple layers of defense against cyber threats. Whether your business will fall victim to a cyber attack is no longer a question of if, it’s when. Because of this, your best defense is an intentional and proactive offense. Using a layered approach to security safeguards your infrastructure from an attacker in ways that traditional security cannot. Under a layered security approach, if an attacker penetrates one layer of defense they will be stopped by the next layer.
[You Might Also Like: Blog Article – “WanaCrypt: How a Layered Approach to Security Protected Prosource Customers From a Global Ransomware Outbreak”]
Planning and implementing a layered security approach means that you will have to deploy security measures that provide protection across all layers of the traditional network computing model. Because of the increased sophistication and frequency of cyber attacks, simply having basic antivirus and firewall security measures is not enough to prevent attacks that can do irreversible damage to your business. You need to deploy a layered security approach to resist and prevent leading cyber threats.
1https://csrps.com/Media/Default/2017%20Reports/2017-Ponemon-State-of-Cybersecurity-in-Small-and-Medium-Sized-Businesses-SMB.pdf